
Is Your Security Team Set Up to Fail? The Risks of Operating in Silos
Modern threats don’t stay neatly in their lanes — so why should your security teams? Many organizations still separate their physical, cyber, and corporate security functions, each operating with its own systems, workflows, and priorities. While this approach might seem organized on paper, it often leaves dangerous gaps in practice. The result? Redundant work, delayed responses, and increased exposure to risk.
To achieve true protection, today’s security operations need convergence via a connected system like Kaseware, where teams share data, workflows, and intelligence through a unified security platform.
Why Siloed Security Teams Are a Hidden Liability
When security teams operate in silos, even the most capable professionals can’t see the full picture. A cyber breach that goes unlinked to an internal fraud case or a physical intrusion tied to stolen credentials are prime examples of how fragmentation obscures connections that matter.
Each security discipline has unique expertise, but when they lack visibility into one another’s data and operations, critical information can fall through the cracks. This lack of coordination not only delays response times but can also compromise investigations, inflate costs, and erode stakeholder trust.
The Cost of Disconnected Systems and Processes
Disconnected systems often mean duplicated work, inconsistent data, and wasted resources. When teams rely on separate tools for incident reporting, investigations, and intelligence gathering, they inadvertently create data silos that prevent timely insights.
Beyond operational inefficiency, these silos carry serious financial consequences. In many cases, organizations that lack cross-departmental collaboration spend significantly more on redundant tools, overlapping training, and time-consuming manual reporting. In high-risk environments, that inefficiency can also translate to regulatory noncompliance, legal exposure, and missed opportunities to mitigate threats before they escalate.
What Security Convergence Really Looks Like
True security convergence unites technology with a broader evolution in organizational culture and operational processes. Once you eliminate common roadblocks, you can align your physical, cyber, and corporate security functions around shared goals, consistent standards, and real-time collaboration.
In a converged model, threat intelligence, investigations, and compliance data live within a single, secure platform. This integration allows decision-makers to connect digital events with physical incidents, uncover emerging patterns, and coordinate responses quickly and accurately.
Unified Systems: A Smarter Path Forward
A unified security platform ensures that every security event, from phishing attempts to facility breaches, is logged, analyzed, and acted upon within a shared environment. This connected approach eliminates data silos, improves situational awareness, and helps teams respond cohesively across disciplines.
Unified systems also simplify compliance by standardizing reporting and maintaining a single source of truth for audits and regulatory reviews. The result? Faster decision-making, stronger coordination, and a measurable reduction in operational risk. This is the goal that many security agencies are aiming to achieve in the coming years.
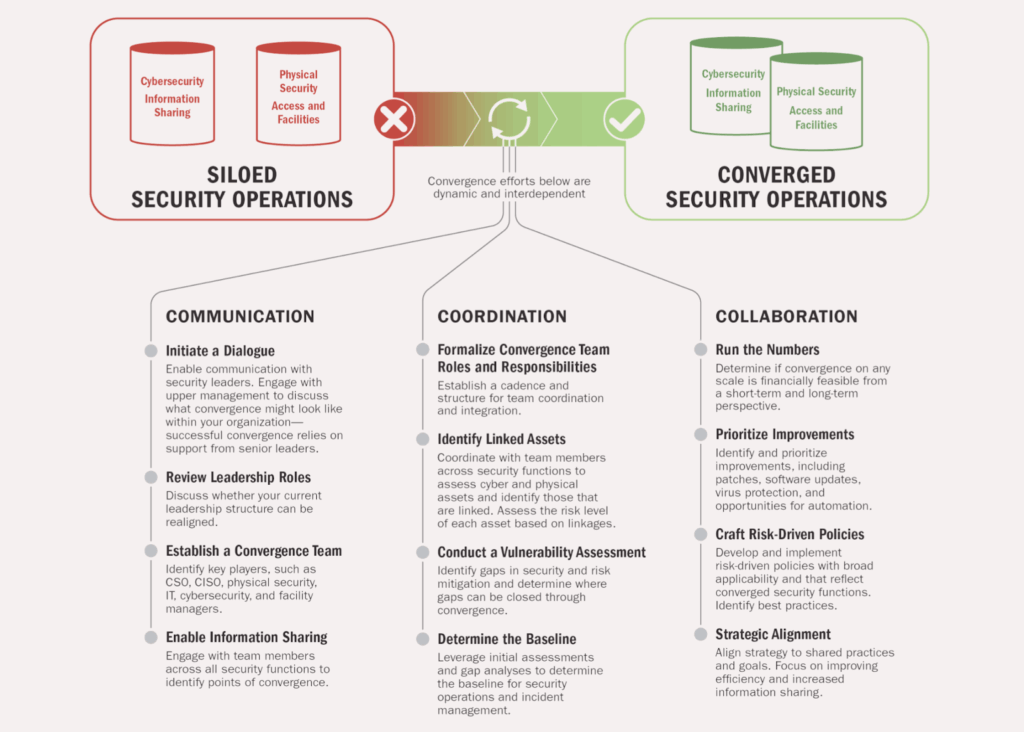
Figure Source: Cybersecurity and Infrastructure Security Agency (CISA). (2021). Cybersecurity and physical security convergence. U.S. Department of Homeland Security.
How Kaseware Enables Collaboration Without Compromise
Kaseware’s integrated investigative platform is designed to help organizations achieve the promise of true security convergence. By bringing incident reporting, case documentation, and investigative intelligence together in one secure environment, Kaseware allows teams to:
- Eliminate Data Silos by centralizing information from across departments.
- Enhance Cross-Departmental Collaboration with unified workflows and shared visibility.
- Strengthen Situational Awareness through real-time analytics and reporting.
- Protect Data Integrity with robust security protocols and user permissions.
Whether you’re managing insider threats, coordinating across multiple facilities, or integrating digital and physical investigations, Kaseware enables seamless collaboration without compromising data security or investigative integrity.
Build a More Connected Future
Security silos are no longer sustainable in an era of complex, interlinked threats. The organizations that thrive will be those that bridge their divides and unify their people, processes, and technologies.
Right now, it’s time to move from isolated systems to integrated investigations.
Request a Demo to see how Kaseware can help your teams collaborate more effectively, respond faster, and secure your operations for the future.








