
Insider Threats Are Evolving. Your Tools Should Too.
Insider threats are more prevalent than ever in today’s complex digital landscape. Organizations face growing risks of internal data breaches, loss, and sabotage. With Kaseware’s insider threat software, you can proactively investigate suspicious behavior—helping protect your data, operations, and personnel from internal risks.
What Is an Insider Threat?
Insider threats occur when individuals within an organization use their authorized access, either intentionally or unintentionally, to cause harm. These threats don’t come solely from employees. Contractors, business partners and third-party vendors who have access to a business’s network, data or systems also pose serious risks.
Detect and Monitor Insider Threats
Organizations can detect and monitor insider threats by deploying a mix of monitoring tools, internal controls, and user education. Key strategies include:
Employee screening
Track digital behavior for red flags like data access anomalies, download spikes, or suspicious logins.
Event auditing
Routine audits help companies understand what regular patterns and behaviors look like so they can recognize potentially fraudulent activity.
Action approval
Implement checks and balances by requiring specific administrators to approve employee actions.
Team training
Teaching employees to avoid fraud, scams and viruses is a proactive way to protect your company from threats.
Threat intelligence software
Use integrated investigation platforms like Kaseware to centralize alerts, collect threat indicators, and link behavior to investigations.
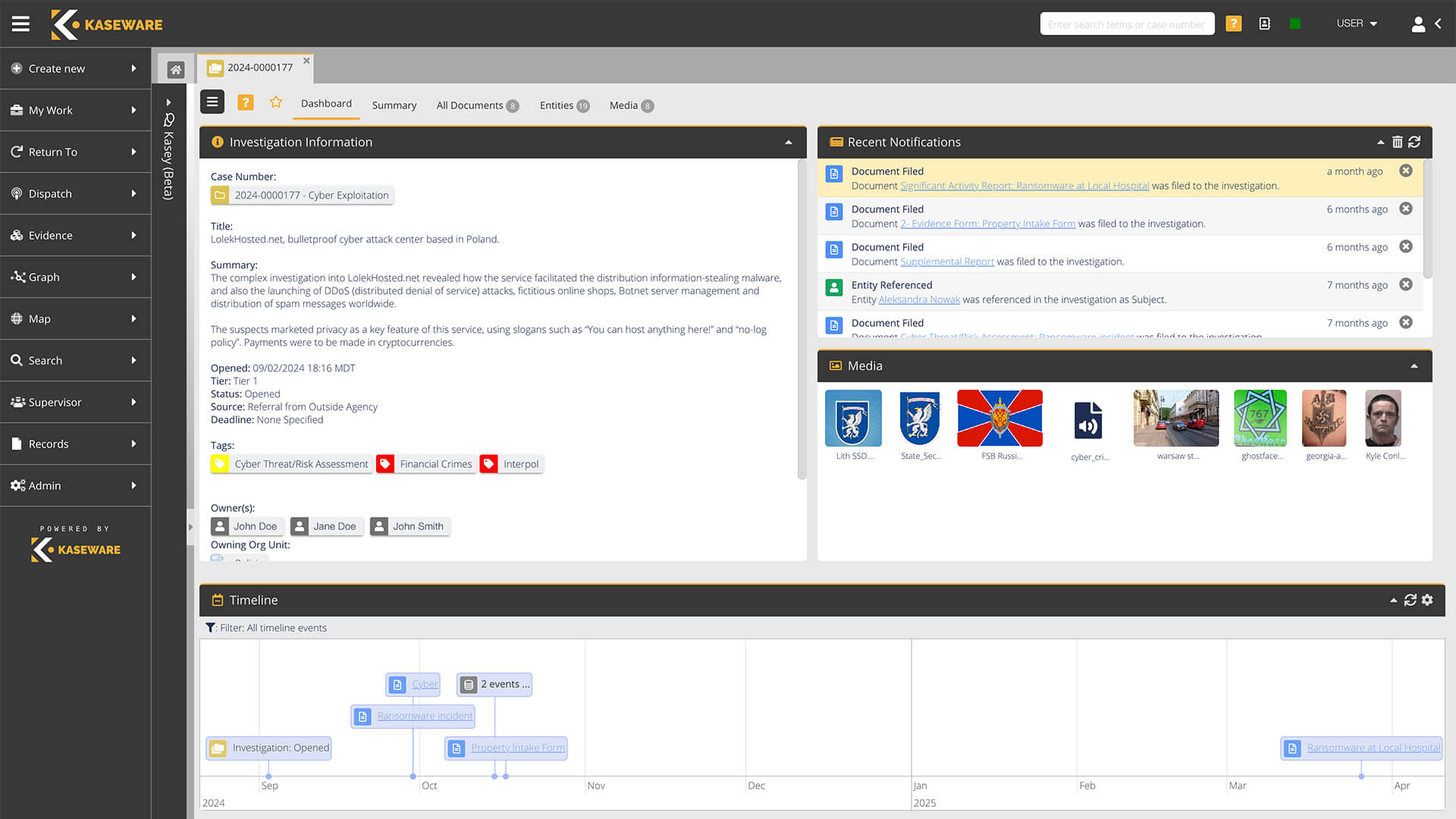
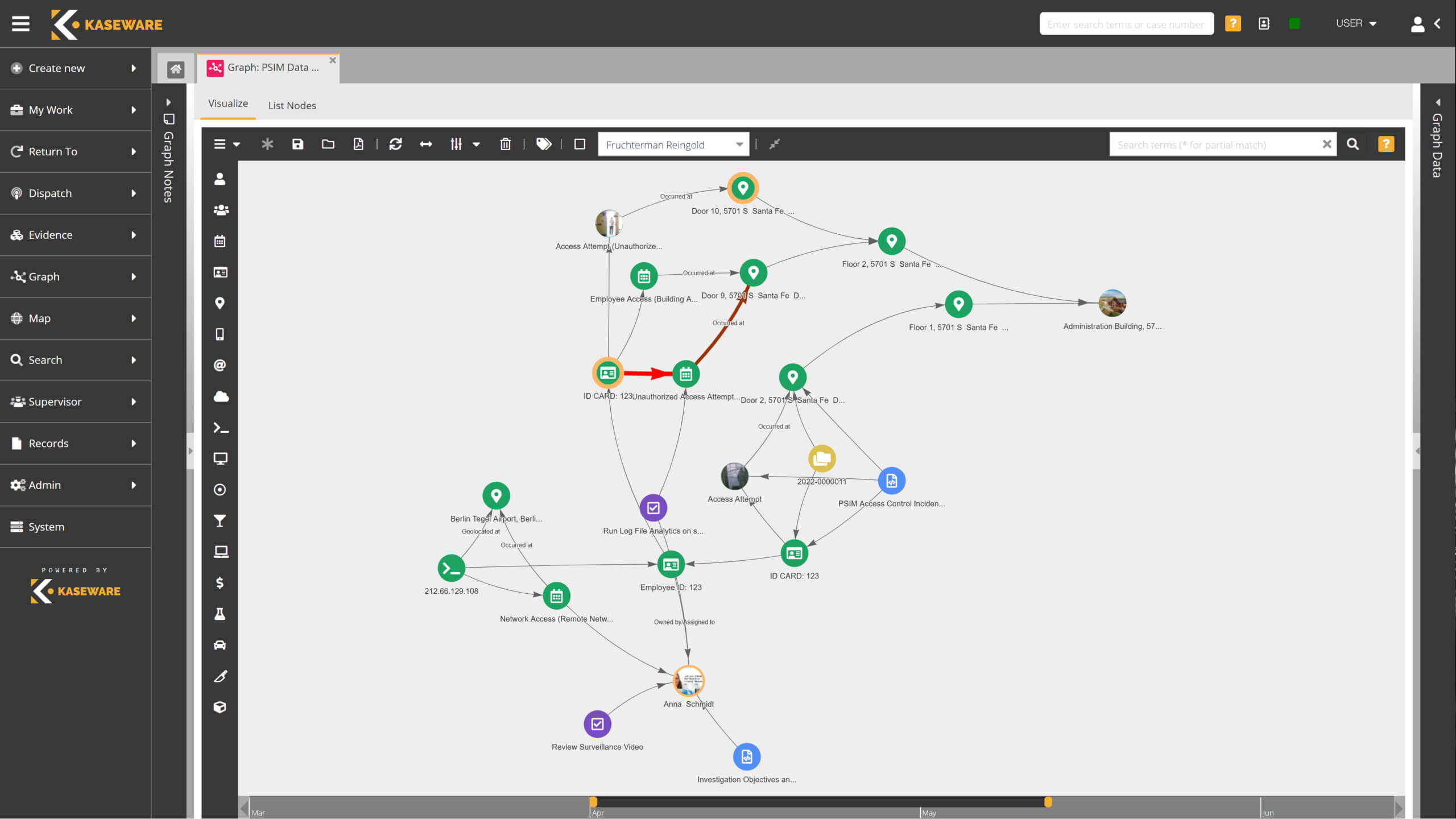
Build a Resilient Insider Threat Program With Kaseware
At Kaseware, we developed threat intelligence software that helps users conduct internal investigations securely and efficiently. Our streamlined platform has dozens of features in one cloud-based source.
Insider Threats FAQs

How does Kaseware help detect insider threats before they escalate?
Kaseware consolidates digital and behavioral data, making it possible to identify suspicious patterns across employees, contractors, and vendors. With automated alerts, link analysis, and dashboards, organizations can surface anomalies early and take proactive action before damage occurs.

Can Kaseware integrate with HR and IT monitoring systems for insider threat detection?
Q2. Can Kaseware integrate with HR and IT monitoring systems for insider threat detection?
Yes. Kaseware’s open API and integration capabilities enable seamless connections to HR, identity management, IT monitoring platforms, and more. This ensures investigations capture the full scope of activity tied to insider risk.

What security measures protect sensitive employee and company data?
Kaseware encrypts all data at rest and in transit, and employs Role-Based Access Control (RBAC) and field-level security. Audit trails, redaction tools, and granular permissions ensure sensitive employee and organizational data remains fully protected.

How can investigations be automated and documented for compliance?
Investigators can leverage workflow automation to route cases, assign tasks, and generate incident reports automatically. Reports can be formatted for compliance and stored with full audit trails, ensuring defensible documentation for internal review or regulatory oversight.
GET A LIVE, CUSTOMIZED DEMO
You can monitor, prevent and resolve threats and investigations within your organization with Kaseware. FBI Special Agents created our streamlined investigative platform to accomplish what other software could not within a single solution.

Fed Time Stories Podcast
Explore the fascinating journeys of former NCIS and Secret Service officials as they transition to the private sector, with humor, insight, and real-world experience from hosts John Gill and Dave Brant.
View Resource








