What exactly is an insider threat?
An insider threat is anyone with legitimate access to your organization’s assets who misuses that access, either intentionally or unintentionally. This could be:
-
Employees
Current or former, disgruntled or simply negligent.
-
Contractors
Temporary workers or third-party vendors with access to your systems.
-
Business partners
Those with privileged access to sensitive information.
Take proactive steps to mitigate insider threats
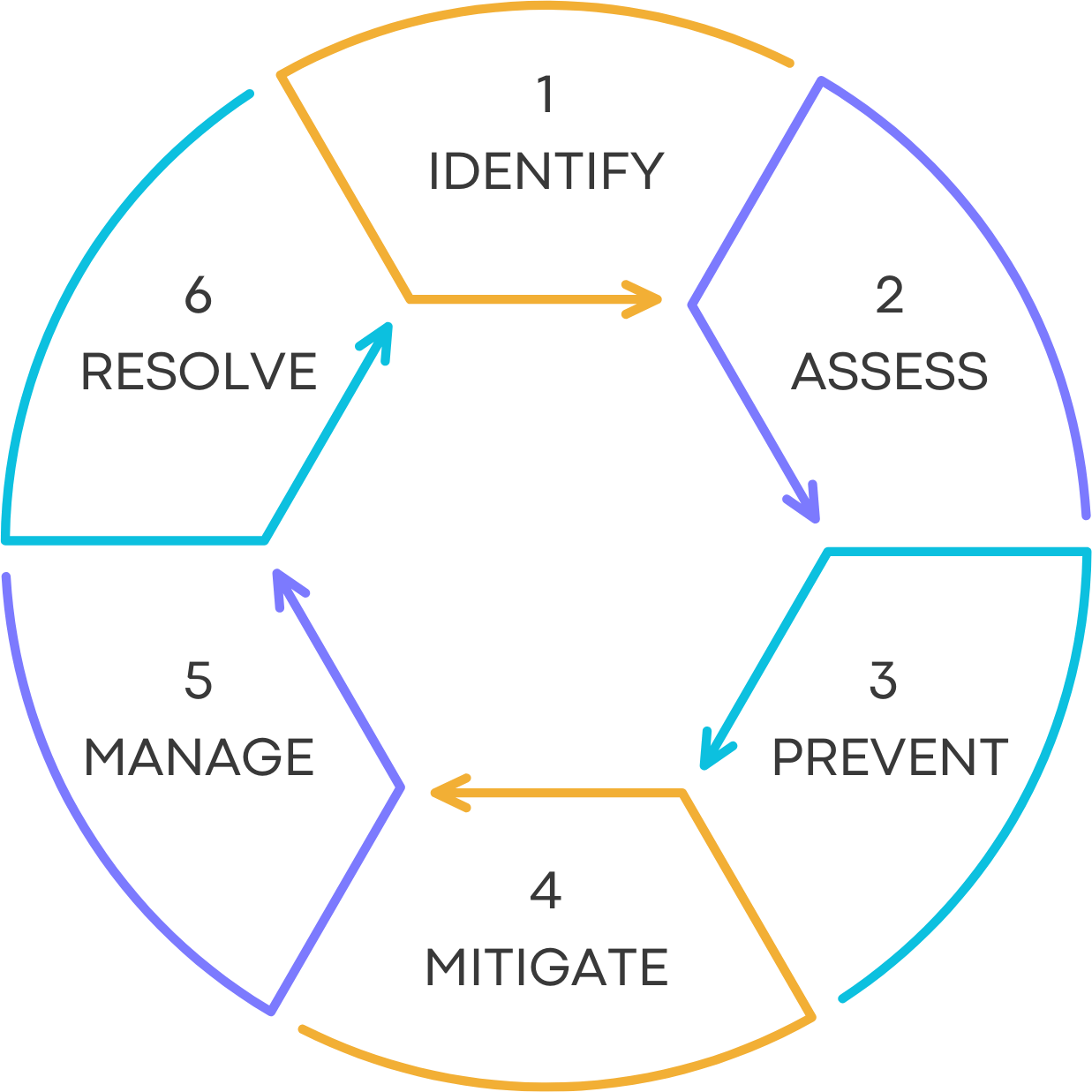
-
Implement strict access controls
Limit access to sensitive data based on the principle of least privilege.
-
Monitor employee activity
Track user behavior and identify suspicious activities.
-
Educate your workforce
Train employees on security best practices and the importance of data protection.
-
Establish a clear insider threat policy
Define acceptable use of company resources and consequences for violations.
-
Conduct regular security audits
Identify vulnerabilities and ensure compliance with security policies.
-
Implement robust data loss prevention (DLP) solutions
Prevent sensitive data from leaving your network.
GET A LIVE, CUSTOMIZED DEMO
You’ll quickly see how Kaseware can improve your investigations and help you achieve mission success.









