Corporate Security Case Management Software, Designed By Former FBI Special Agents
Kaseware was developed by the same team behind the FBI’s global investigative case management system, bringing over 100 years of combined experience and leading diverse teams to success in law enforcement and intelligence communities.
Corporate security software is essential in today’s world, where organizations face increasingly sophisticated threats to their assets, employees, and data. By combining necessary tools into a single platform, it allows companies to proactively address risks, ensure compliance, and maintain business continuity.
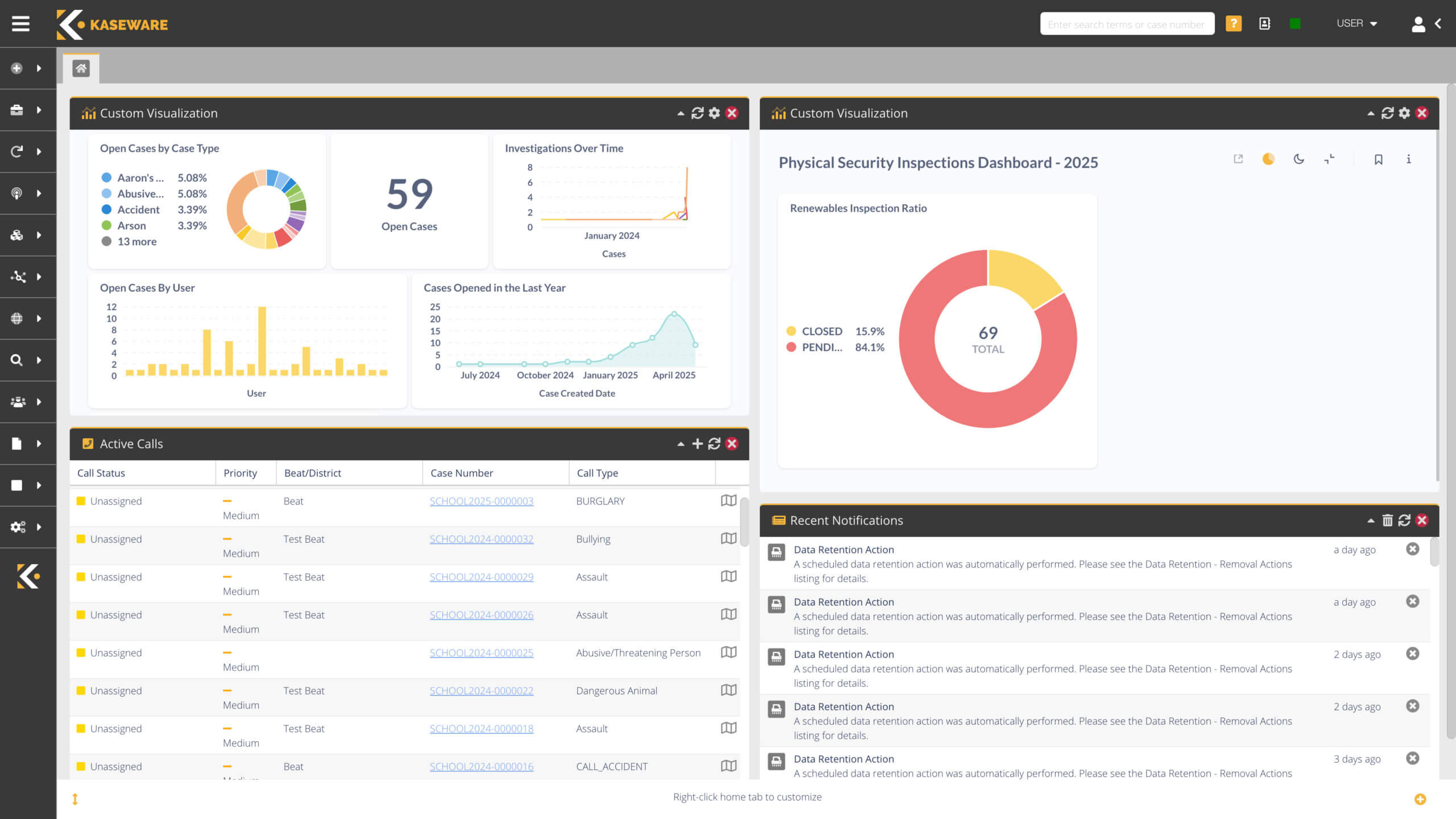
Unleash the power of Kaseware’s world-class security platform—an all-in-one solution combining investigative case management, incident management, analytics, intelligence collection, collaboration tools, and more. With everything in one seamless system, your teams can better protect your assets, mitigate risks, enhance duty of care, identify threats, and find threat actors.
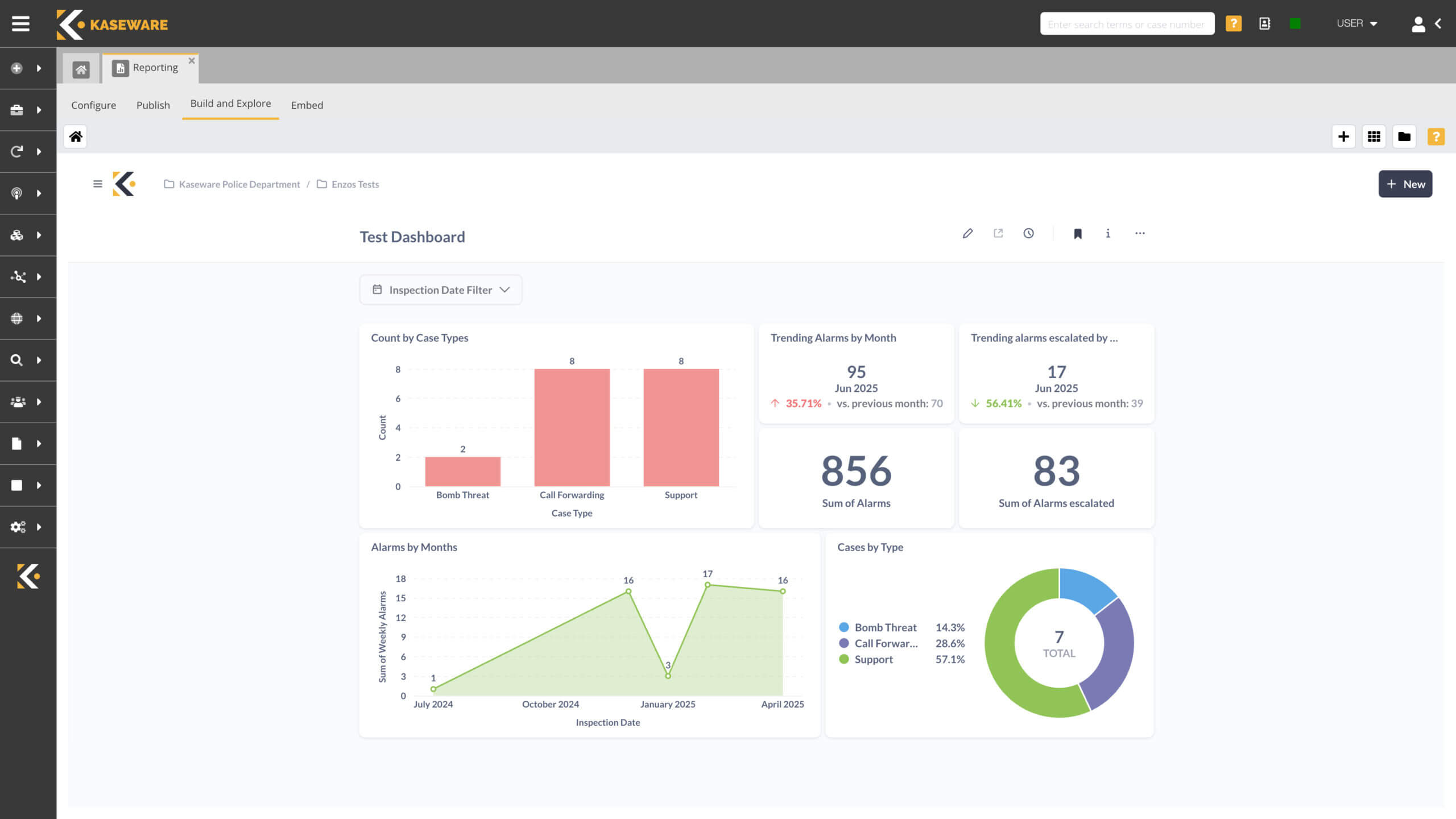
CUSTOM WORKFLOWS, ANALYTICS & REPORTING, TASK MANAGEMENT
A simple system for teams of any size
- Increase efficiency with customized workflows & forms
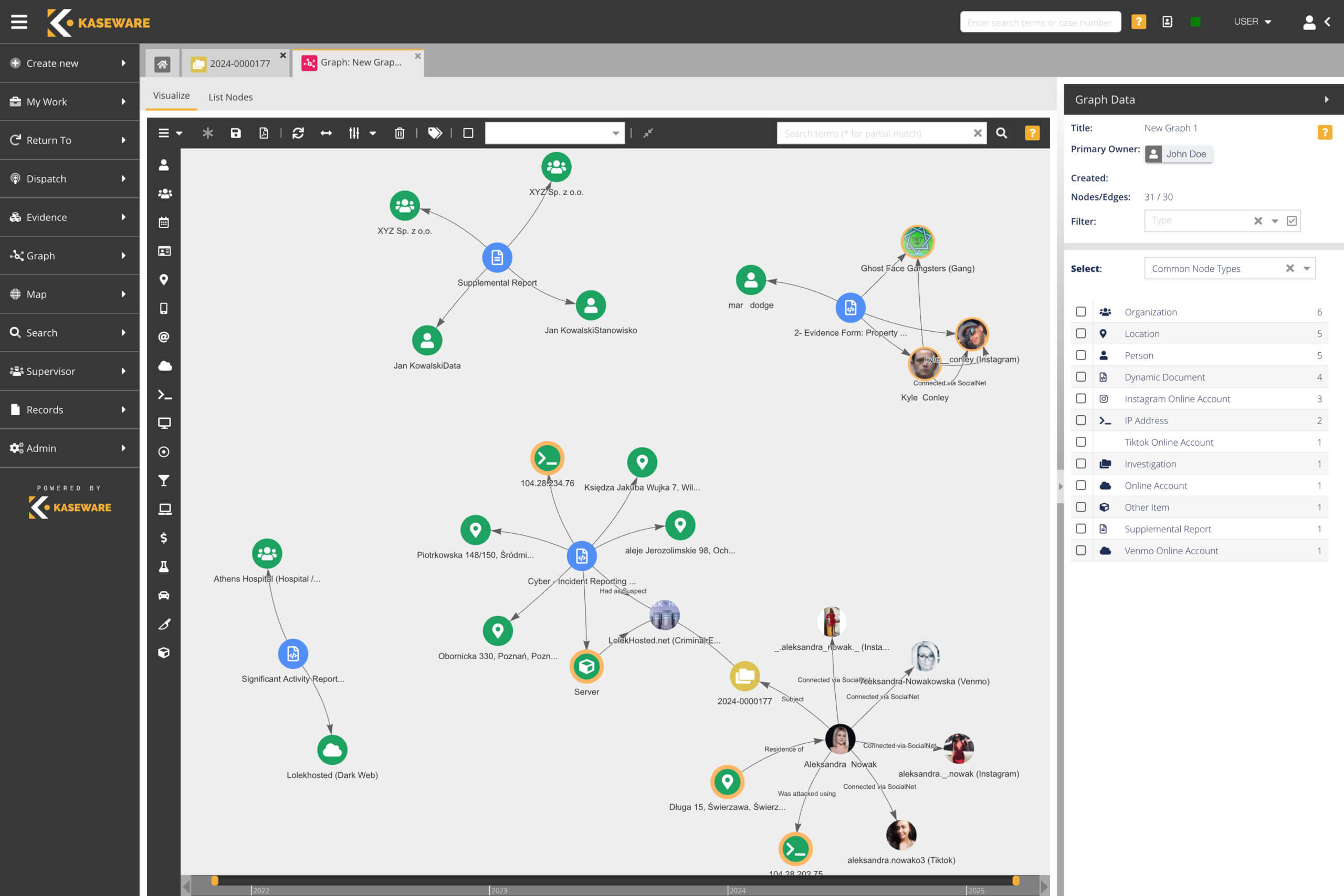
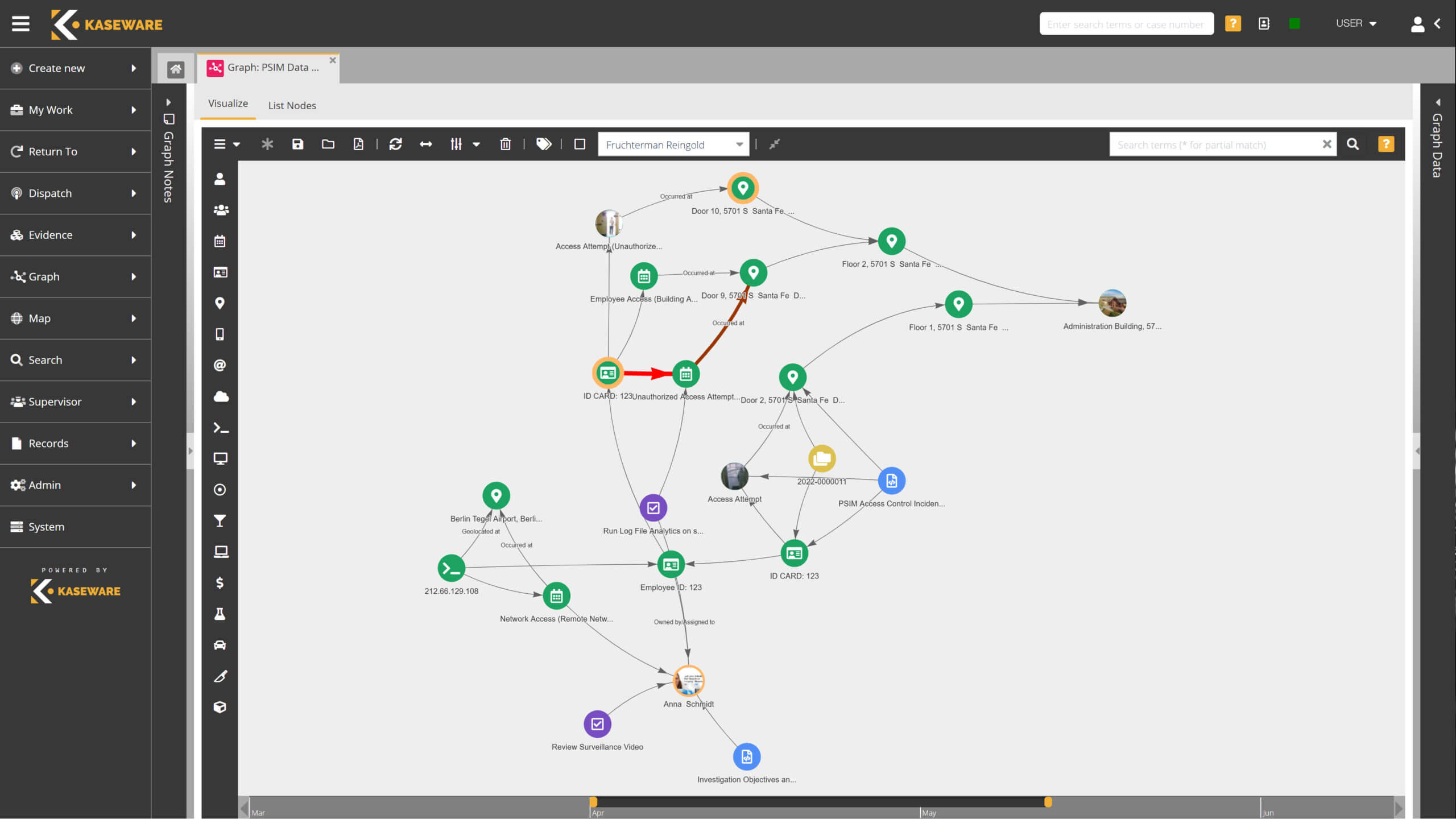
- Uncover connections with automatic graphing & link analysis tools.
- Collaborate seamlessly with task management & notification tools.
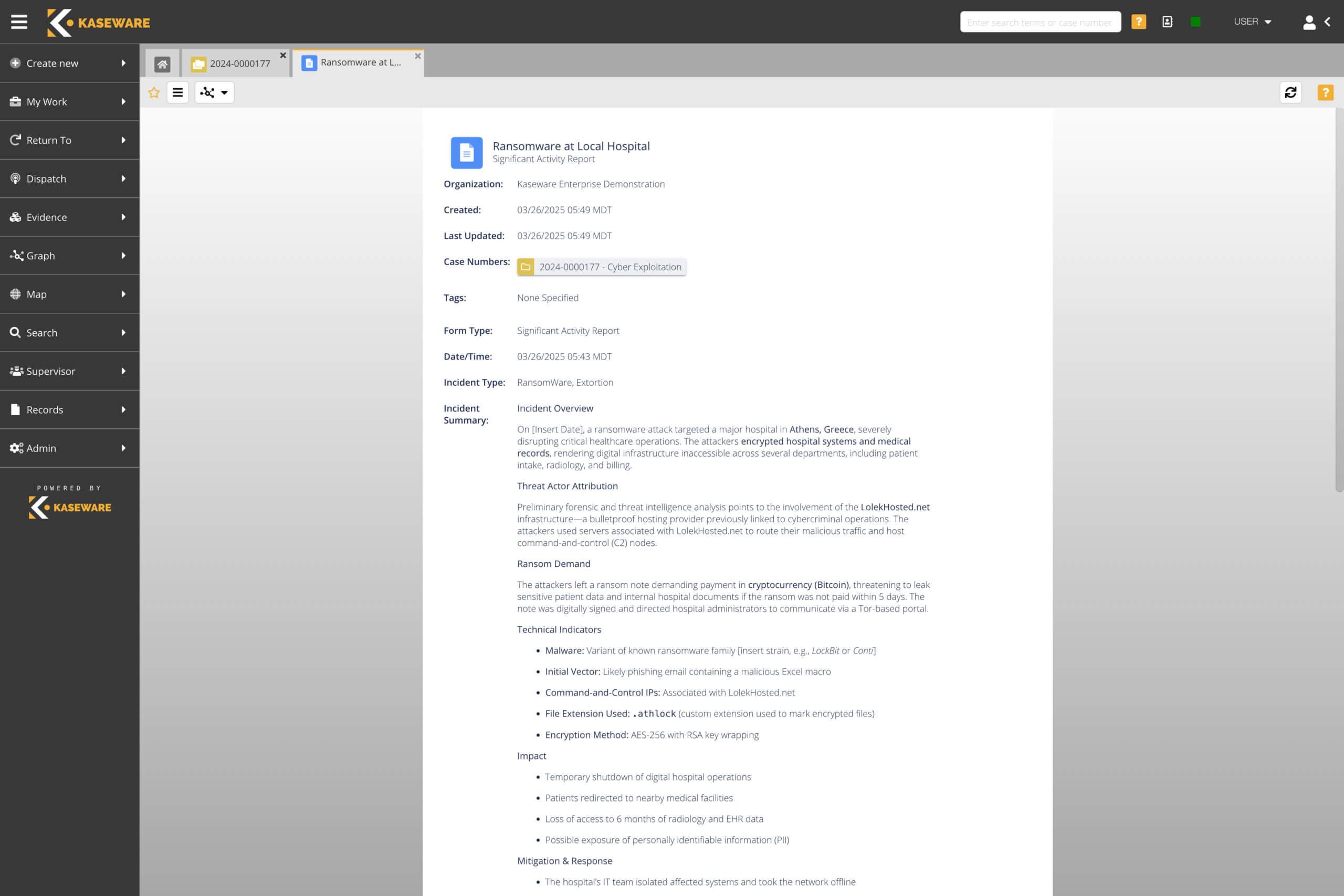
FRAUD & COMPLIANCE, ORGANIZED RETAIL CRIME, CYBER SECURITY
Close cases more efficiently than ever before.
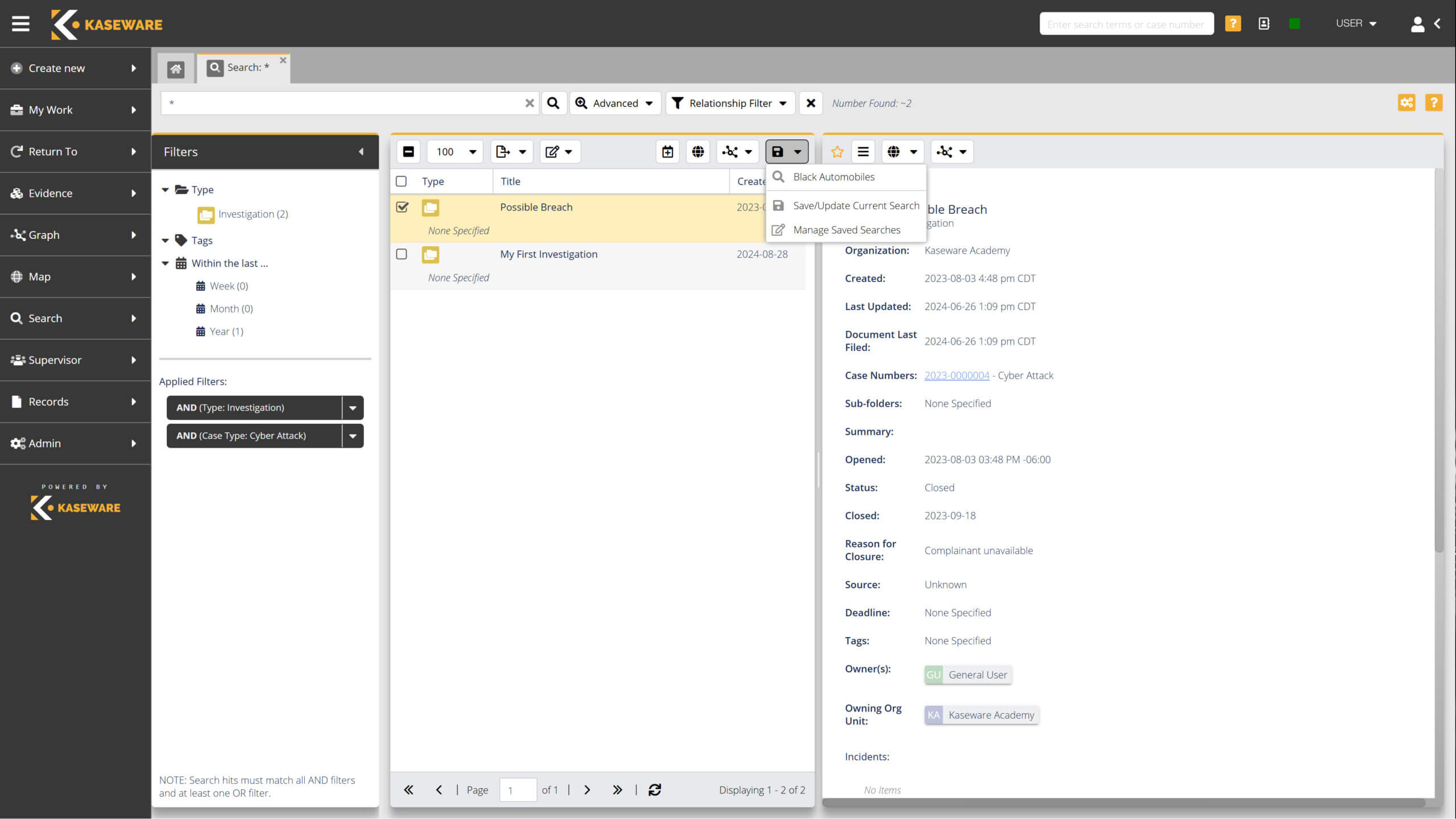
- Reduce risk by centralizing all intelligence in one place.
- Easily migrate data for analysis to identify sources of fraud and loss.
- Directly search and analyze Open Source Intelligence (OSINT) sources.
INVESTIGATIVE TOOLBOX, LINK ANALYSIS, OSINT
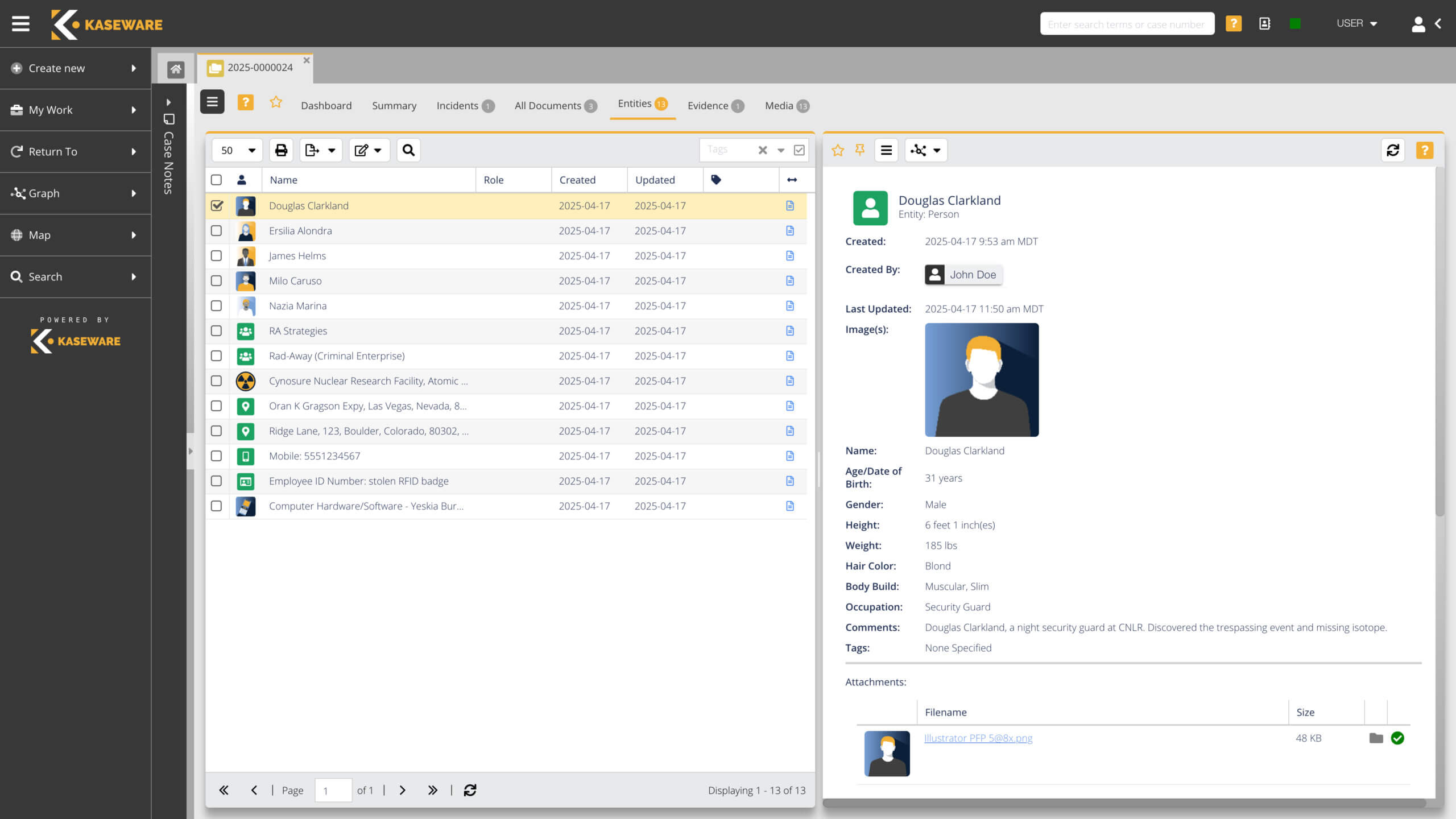
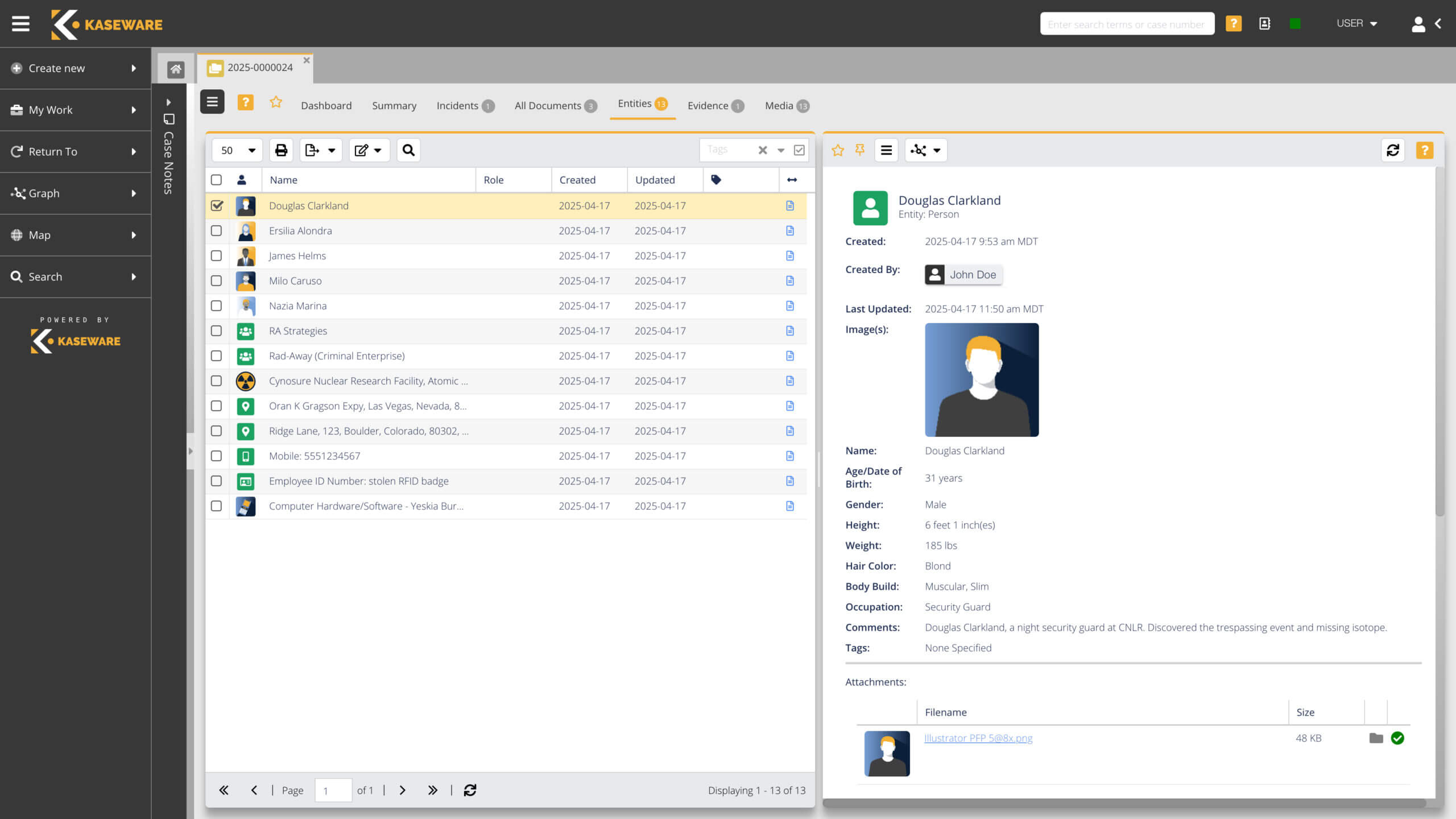
World-class investigation management for today’s ever-evolving threats.
- Mitigate risks and investigate fraud with cutting edge analytical tools.
- Centralize all your data—SIEM, GSOC, OSINT, forensics, disc images and more.
- Search in real-time nearly every social media and deep web source.
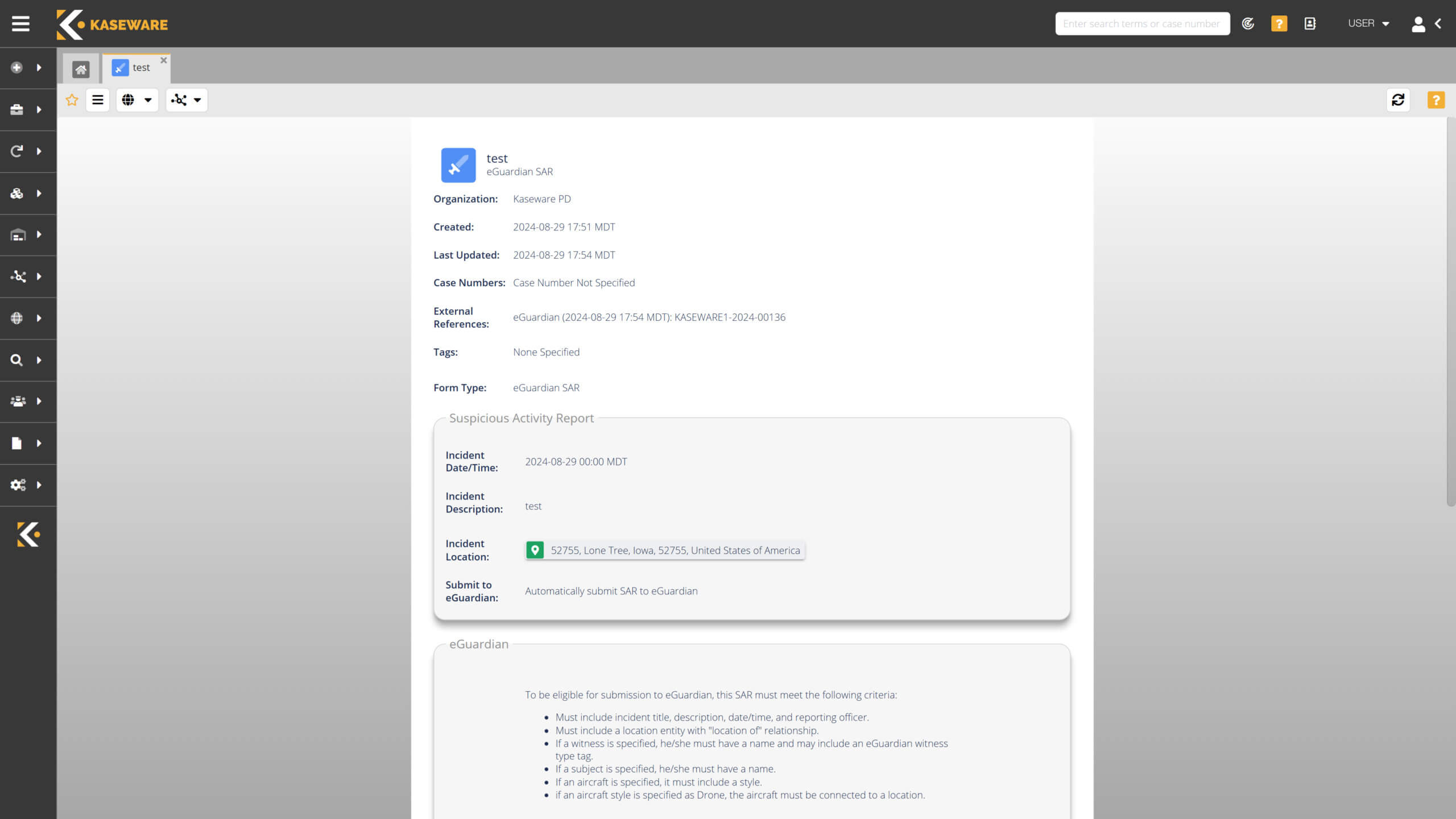
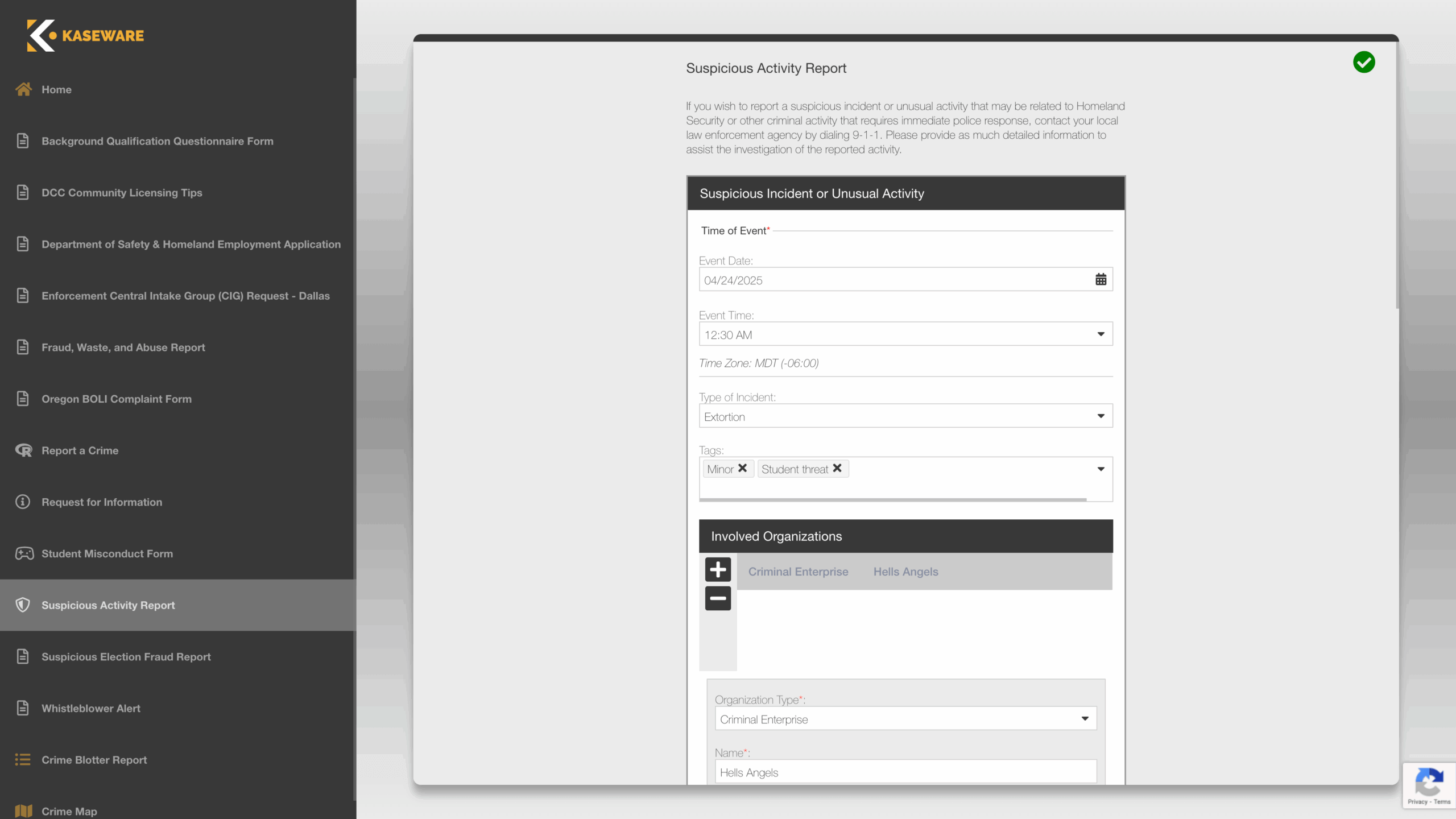
EXECUTIVE PROTECTION, THREAT DETECTION, ALERTS & REPORTING
Protect your team with world class intelligence.
- Enhance your duty of care with automated threat monitoring tools.
- Customizable web portals for the public to submit valuable information.
- Securely collaborate with layers of access controls and document classification.
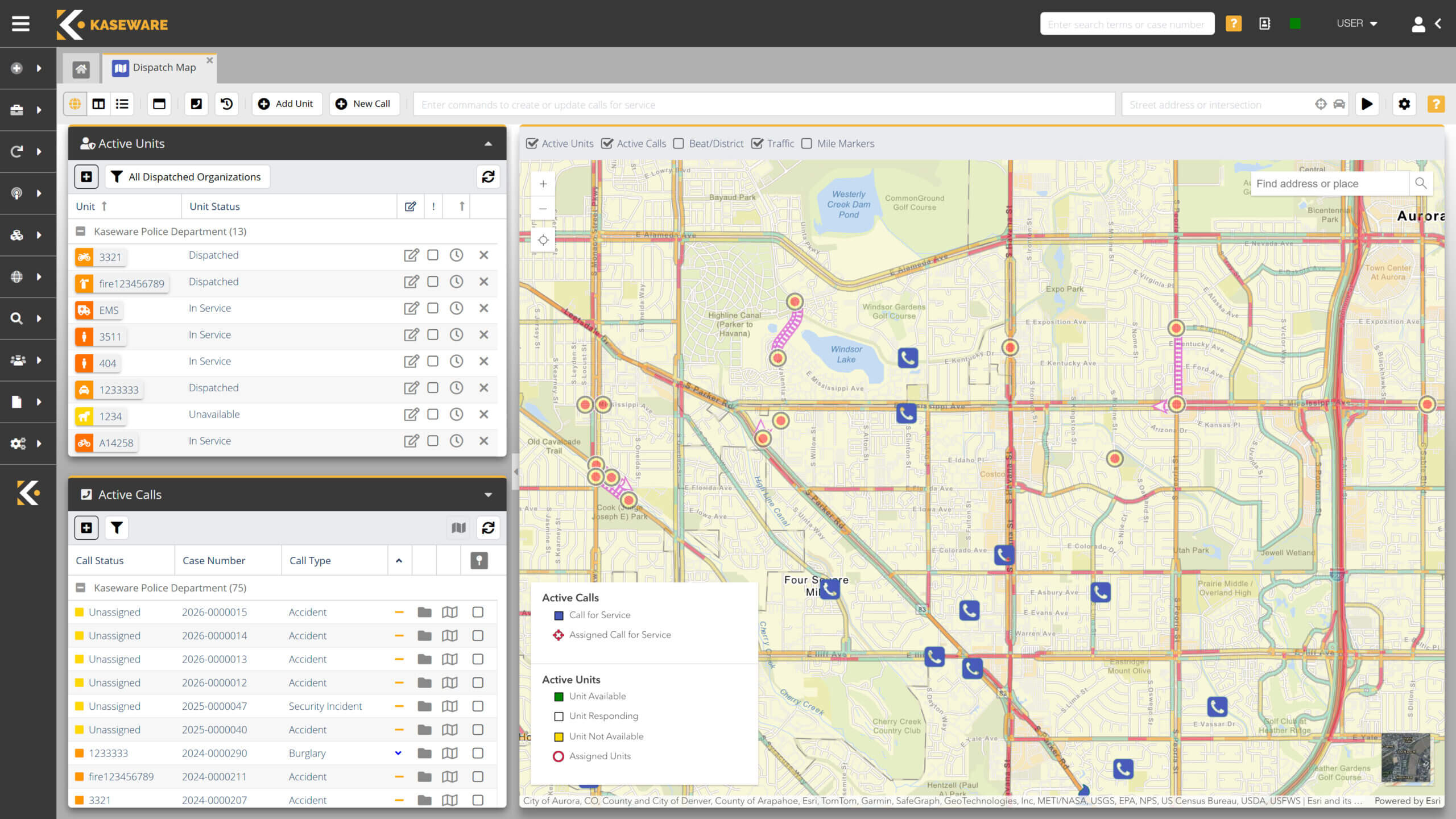
INCIDENT MANAGEMENT, DISPATCH & REPORTING, IOS & ANDROID APPS
Easily manage a guardforce of any size.
- Dispatch and manage security incidents in any area of the world.
- Complete field reports from your phone, along with GPS tracking, directly within the CAD system.
- Seamlessly transition dispatch data to supplemental cases.
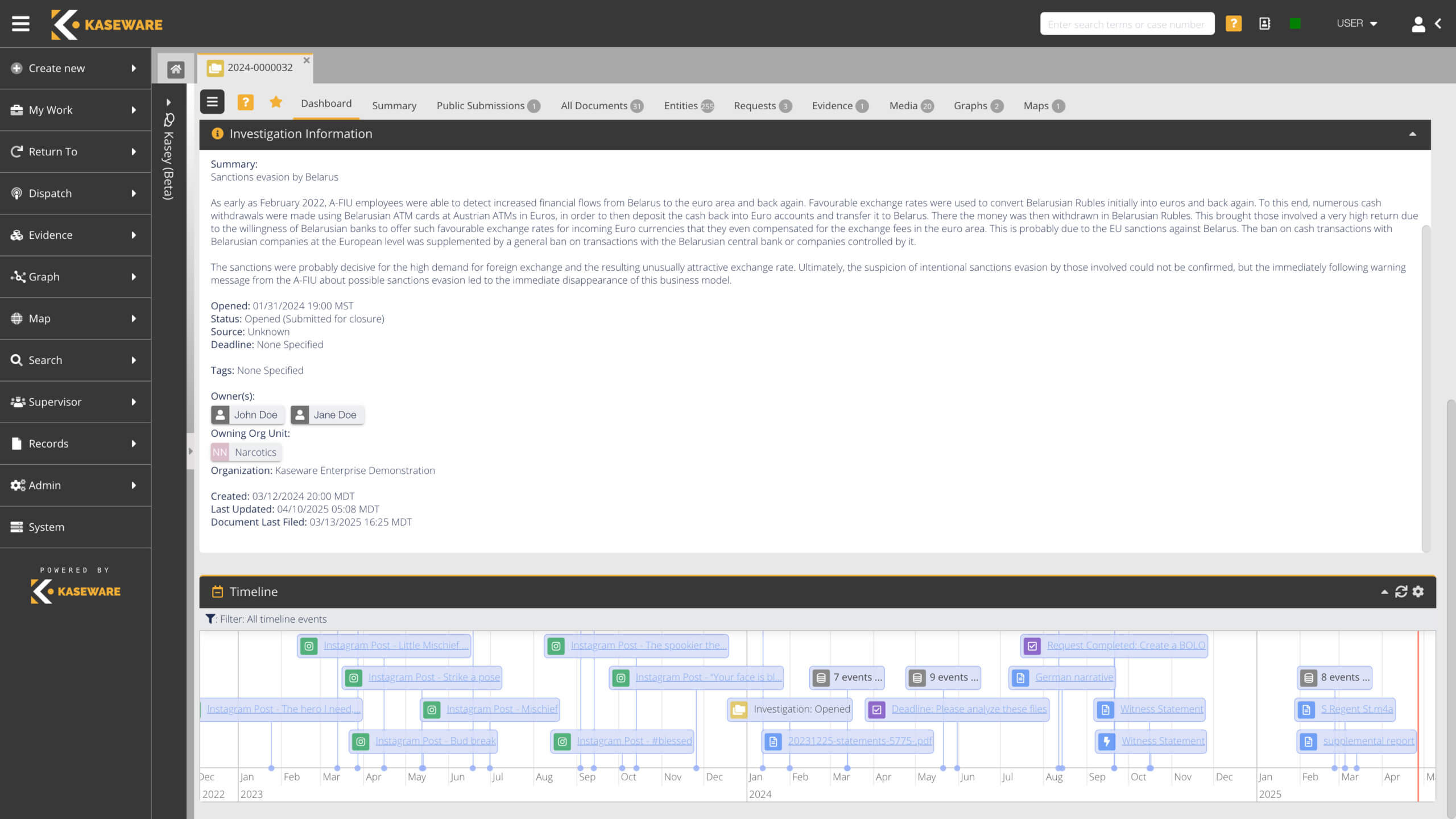
Corporate Security Case Management System
Give your teams access to the ultimate corporate security software. Manage operations, easily document everything as well as streamline processes using a flexible, configurable, and powerful investigative case management toolbox.
Modernizing Corporate Security Operations
When the safety of your business, employees, and customers is at stake, Kaseware gives you the tools to fight back. Leveraging modern capabilities, you’ll be able to react to security risks, manage cases from start to closure, and take steps to prevent future incidents.
- AVIATION
- ENERGY & UTILITIES
- PHARMACEUTICAL
- FINANCE

Secure the Skies
Take proactive steps to maintain ongoing regulatory compliance and respond to security threats in real time.
Power Operational Efficiency
Prevent service interruptions and noncompliance penalties with data monitoring and alerts for both physical and cyber threats.

Remedy Issues and Restore Stability
Protect your brand and assets and transform your investigative processes to close cases quicker, identify trends, and safeguard assets.

Diversify Threat Response Capabilities
Preserve confidence in your institution with purpose-built investigation management software that can adapt to changing security needs.
Corp Sec FAQ

What types of corporate security challenges does Kaseware help solve?
Kaseware supports investigations into fraud, insider threats, executive protection, and cybersecurity incidents. It unifies your tools and data into a single platform to streamline response and decision-making.

Can Kaseware integrate with our existing security systems?
Yes, Kaseware offers robust integration capabilities, allowing it to connect with your current systems such as OSINT platforms, visitor management systems, and more.

Is Kaseware suitable for organizations of all sizes?
Absolutely. Kaseware is scalable and flexible, serving both mid-sized businesses and large enterprises. It’s configurable to match the complexity and structure of any organization.

How does Kaseware enhance incident response times?
With real-time collaboration, automated workflows, and mobile access, Kaseware allows your team to respond faster and more effectively, reducing time lost to manual coordination.

What security standards and certifications does Kaseware comply with?
Kaseware is ISO 27001 and ISO 27701 certified, ensuring high standards for data protection and privacy compliance.

Can Kaseware be customized to fit our specific workflows?
Yes. The platform supports low-code/no-code configuration, so you can tailor workflows, forms, notifications, and access controls to suit your operational needs—no development required.

Does Kaseware support mobile access for field operations?
Yes, Kaseware offers mobile apps for iOS and Android. Your team can report, track, and manage incidents from anywhere, whether they’re in the field or at headquarters.
GET A LIVE, CUSTOMIZED DEMO
You’ll quickly see how Kaseware can improve your investigations and help you achieve mission success.